Locky Ransomware: Know everything about this new malware

The Government of India (Computer Emergency Response Team (CERT-In) has issued an alert on the spread of a new malware which is known as ‘Locky Ransomware’. Locky is very similar to WannaCry in the way it caused massive uproar around the world. Locky Ransomware can lock computers and a ransom demand is raised to unlock them. (Ransomware is a malicious software) and it is learnt to demanding ransom of half a bitcoin, which at present rate is equivalent to over Rs 1.5 lakh. The system infected by Locky Ransomware gets locked or encrypted with random numbers with “extension [dot] lukitus or [dot] diablo6”. The instructions contain installation of “a TOR browser and visiting (dot) onion sites and demanding ransom of .5 Bitcoins”, according to the alert issued.
This is done through spam mails which are circulating with common subject lines to spread variants of Locky Ransomware. These messages contain common subjects like ‘please print’, ‘documents’, ‘photo’, ‘Images’, ‘scans’ and ‘pictures’. However, the subject texts may change in targeted spear phishing campaigns.” The severity of the ransomware is treated as “HIGH”.
Cybersecurity company AppRiver said that it has seen over 23 million messages sent in the attack, making it one of the largest malware campaigns seen so far.
How does this happens?
1. You receive an email, with an attachment that when opened is a scrambled mess of words.
2. At the top are the words, ‘Enable Macros if the data encoding is incorrect.’
3. The moment you enable macros, instead of correcting the document, your system gets encrypted and Locky ransomware is activated and Windows ability to take live backup called Shadow copies is also compromised.
4. Your wallpaper changes to ‘How to decrypt’ message displaying image.
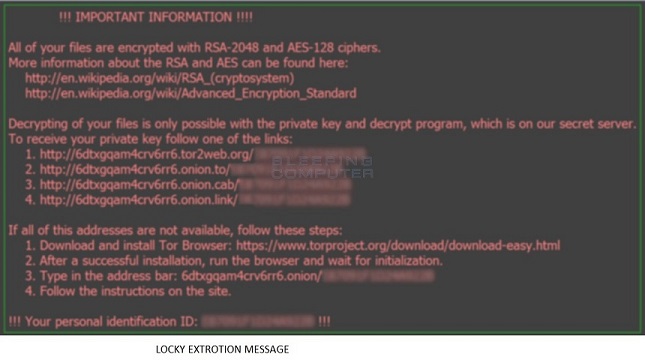
The spam mails also contain links to fake dropbox websites which are being used to spread Locky variants.
How can we protect our computer from ransomware?
Here is a list of recommendations advised to the users to prevent Locky from compromising your computer.
• Never open any spam emails, or attachments as well as update anti-spam and block lists.
• Block malicious IP addresses.
• Do not download or open attachments which contains Zip files.
• Perform regular backup of your data, and store it on some other devices most preferably offline.
• Disable Macro in Microsoft Office applications ‘Disable all macros with notification’. Macros can run in Ms. Office applications only if the Macro settings are set to ‘Enable all macros’ or if the user manually enables it. This is done so because the email attachment comes in Macro Enabled form.
• Have an updated Antivirus installed on your personal as well as office systems.
• Don’t click on unnecessary popups while visiting websites which may contain Embedded JavaScript (.js) file which can download the ransomware.
• Don’t use administrative accounts for carrying out Business as Usual activities, which limits the rate of installation. Also disable remote Desktop Connections.
• Don’t visit malicious websites or blocked websites listed on the advisory at least.
• Update your operating systems, third party applications like browser, browser plugins and anti-virus software for latest security patches.
Practice all the above recommended. In spite of this, if you suspect your computer system has been infected, contact your IT team and under no circumstances pay any ransom.
Generic Prevention Tools are available at the following website.
Source: Alert issued on Cyber Swachhta Kendra i.e. at http://www.cyberswachhtakendra.gov.in/alerts/locky_ransomware.html
